Public websites and forums
Information from company websites, forums, and bulletin boards can provide insights into the technologies used, internal structure, and potential security weaknesses.

CONGRATULATIONS!
Open Source Intelligence (OSINT) is a crucial aspect of ethical hacking, providing valuable data through publicly available sources. Ethical hackers utilize OSINT to gather information that helps in identifying potential vulnerabilities and enhancing security measures. This page includes a few tips, tool, and techniques used in OSINT for ethical hacking.
OSINT refers to the process of collecting data from publicly accessible sources to be used in an analysis context. In the realm of cybersecurity, ethical hackers use OSINT to collect data about a target organization without breaching any laws or policies.
Techniques Employed in OSINT for Ethical Hacking
- Social Media Analysis: Examining social media platforms to gather data about individuals or organizations. This can include details on personnel, internal activities, and more.
- Domain and Network Analysis: Using tools like WHOIS and DNS queries to gain insights about domains, associated IP addresses, and the network infrastructure of a target. Go to https://hackerrepo.org for more tips and tools
- Geolocation of Assets: Identifying the physical location of networked assets such as servers and offices. This can help in understanding the geographical spread of a network.
- Metadata Analysis: Analyzing data embedded in media files and documents. Metadata can reveal the authorship, location, and software used, providing further insights into the security posture of the target.
NOTE: While OSINT involves publicly available information, ethical hackers must adhere to ethical guidelines and legal boundaries. The information gathered should only be used to improve security measures and not for causing harm or invading privacy.
Additional OSINT tips:
Information from company websites, forums, and bulletin boards can provide insights into the technologies used, internal structure, and potential security weaknesses.
Government and public records: Databases and records available from government agencies can provide information on domain registrations, patents, and more that are useful for mapping out an organization's online presence.
Databases like Shodan and Censys allow researchers to search for internet-connected devices, including potentially vulnerable systems exposed online.
Passive Recon == OSINT. Passive reconnaissance refers to an information gathering technique that involves tools that do not directly interact with the target device or network. There are different approaches to passive reconnaissance, such as utilizing third-party databases or employing undetectable tools that listen to network traffic and intelligently deduce information about device communication. This method is non-invasive and unlikely to cause disruptions or crashes, making it ideal for scenarios where system stability is crucial, like analyzing a production network. Passive reconnaissance operates stealthily, producing no noticeable traffic or network alerts. The choice of passive reconnaissance technique depends on the desired information. Developing a solid methodology is essential in penetration testing to select the appropriate tools and technologies for the engagement.
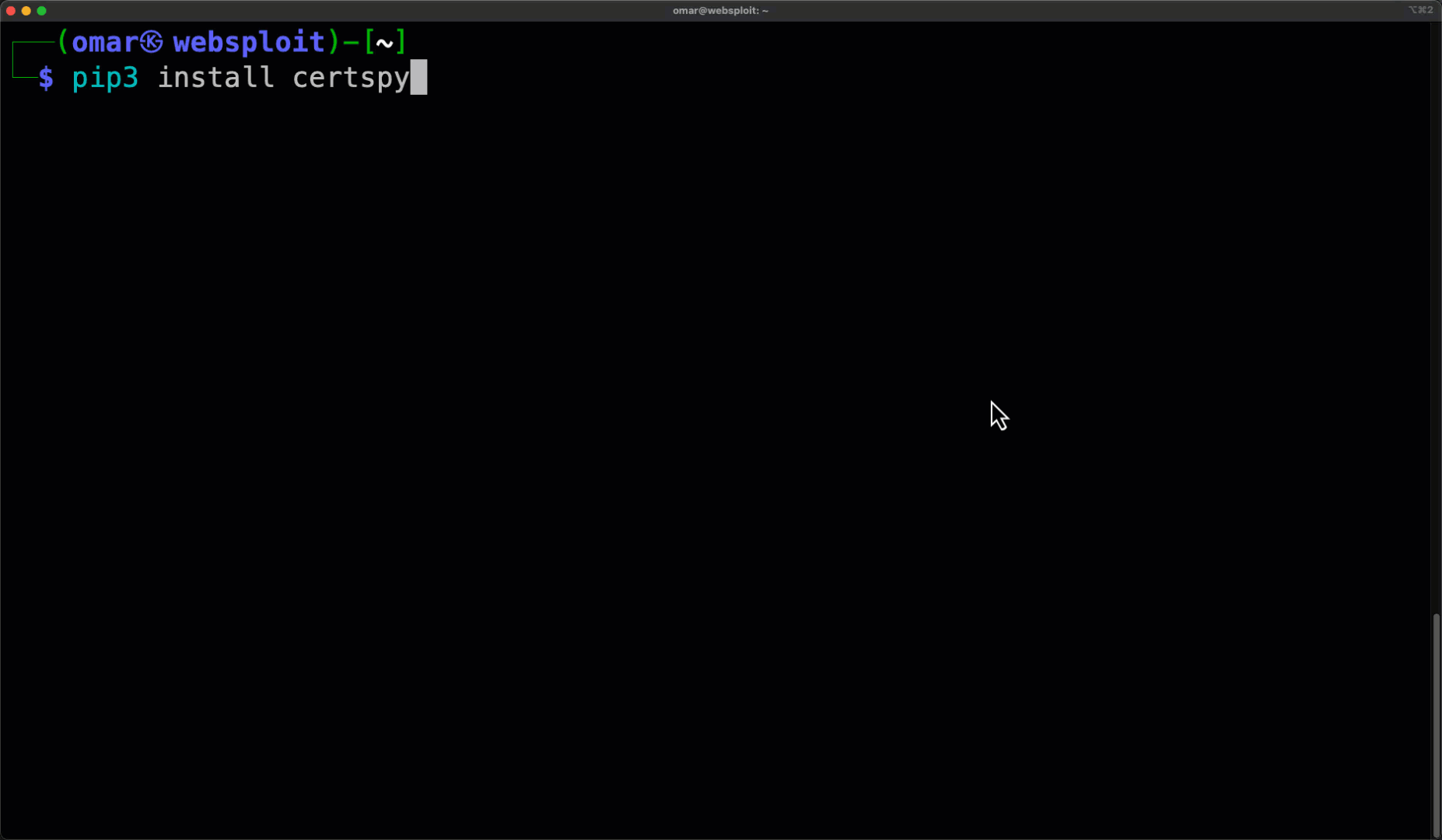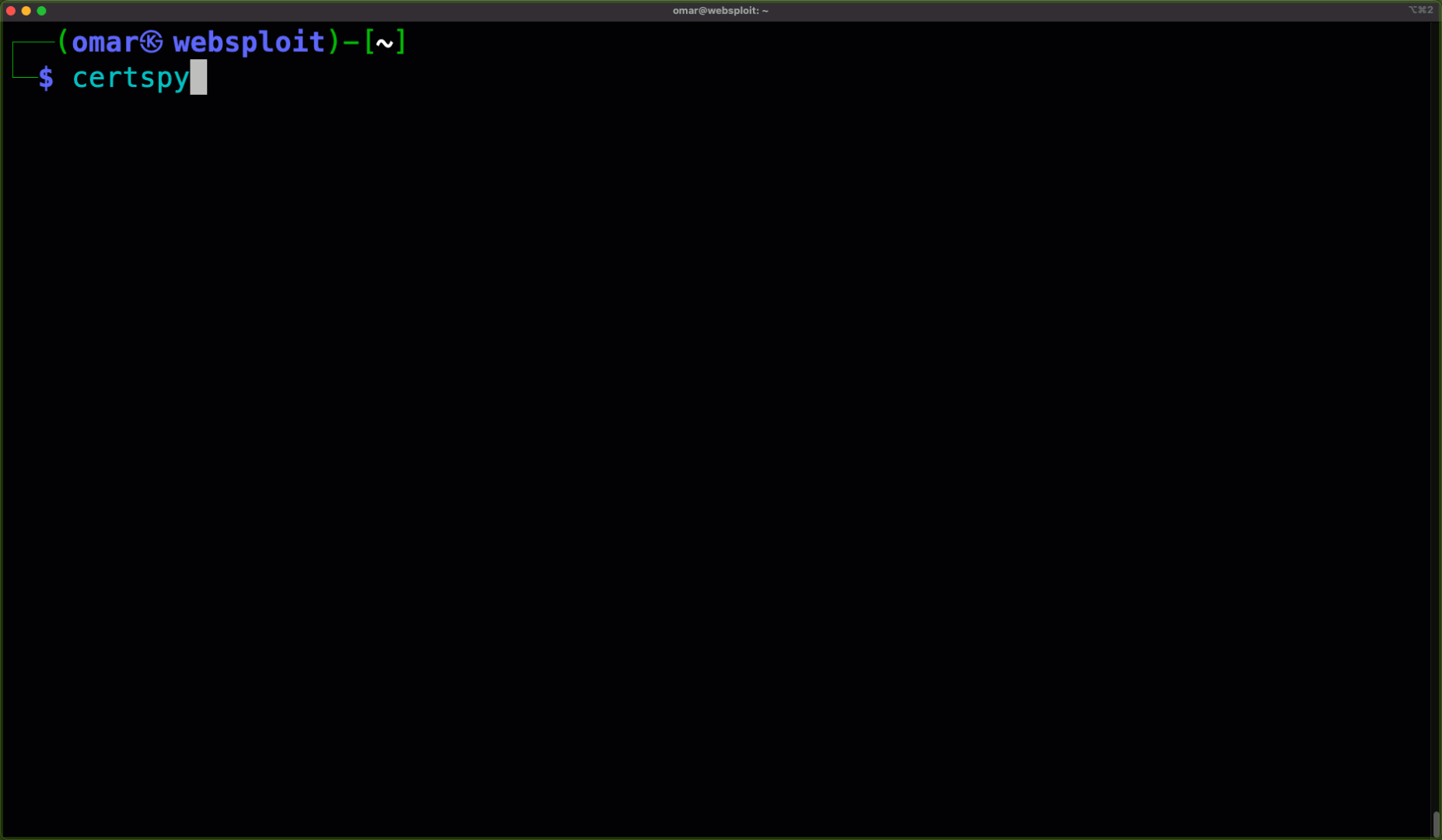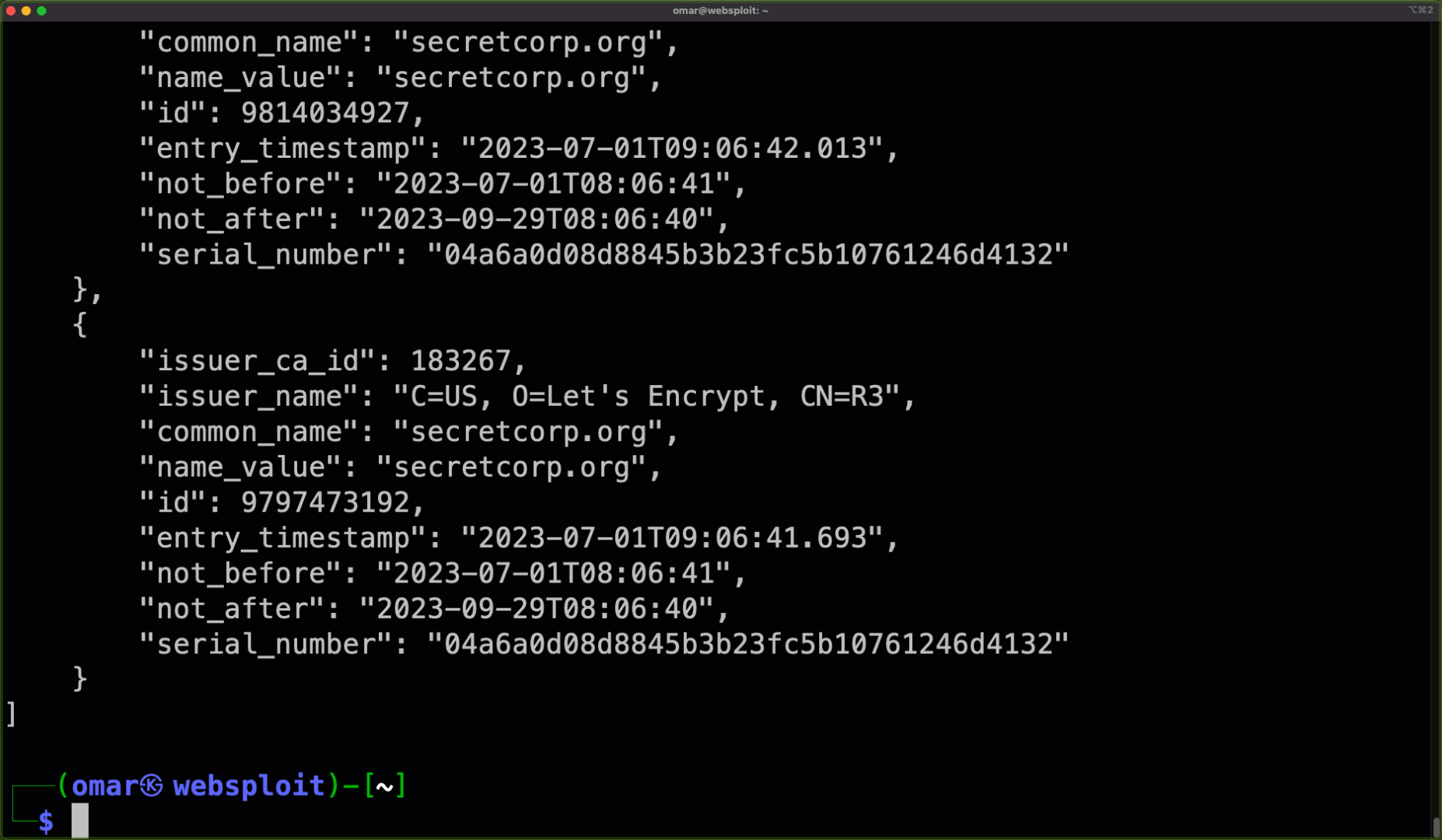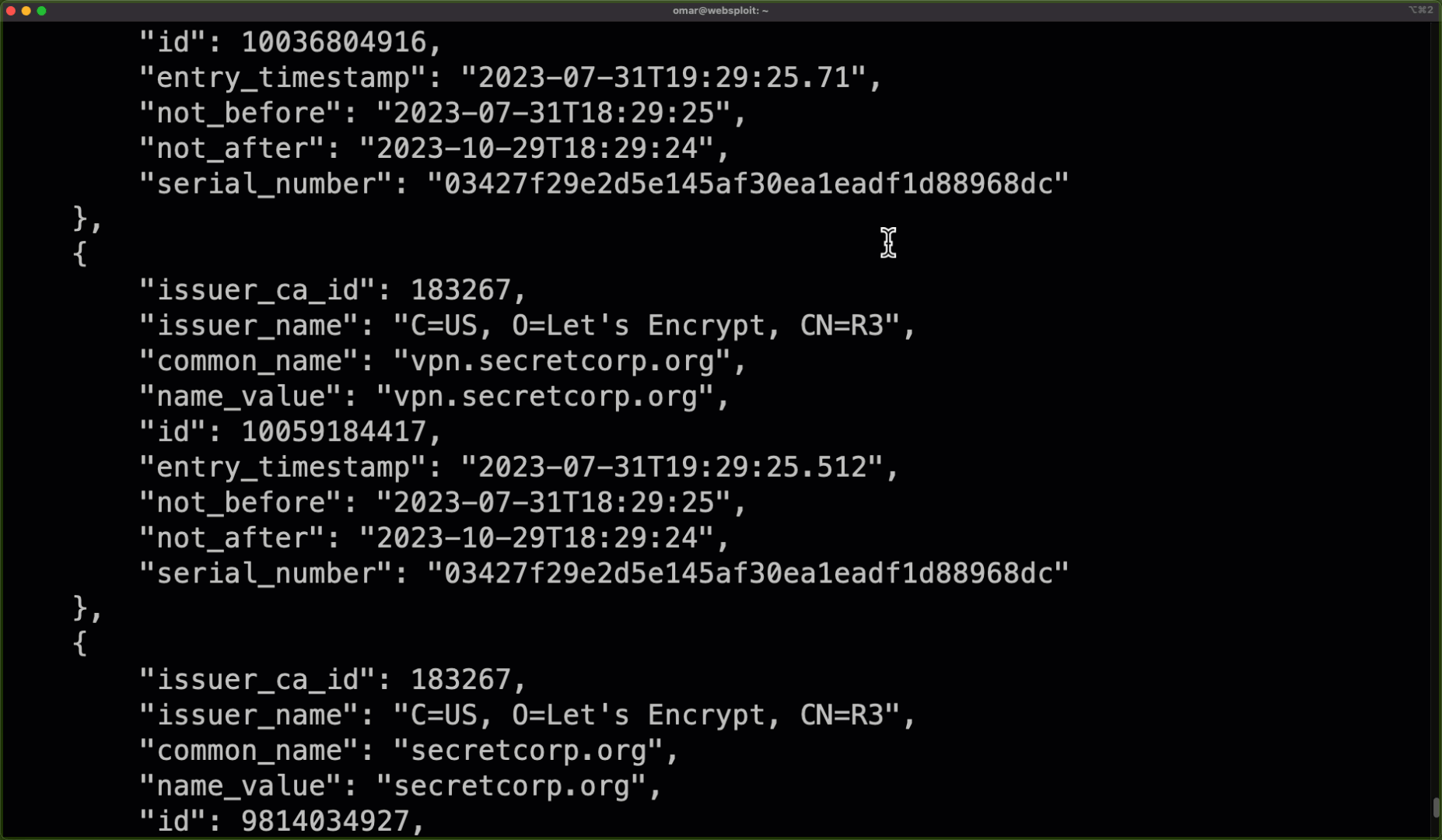
Certificate Transparency (CT) is a security standard and set of protocols that aims to increase transparency and accountability in the digital certificate issuance process. It is designed to make it more difficult for attackers to obtain fraudulent certificates for domain names, and to make it easier to detect and revoke such certificates if they are issued. This is achieved by creating a public, append-only log of all digital certificates issued by a certificate authority (CA), which can be audited by anyone. CT logs are used to verify that a certificate was properly issued by a CA and has not been revoked.
CT can be used for passive reconnaissance and OSINT. There are several websites that provide information and tools related to certificate transparency:
1. crt.sh - This website allows you to search for certificates in various CT logs and view the details of each certificate.
2. CertSpotter - This website allows you to monitor certificate transparency logs for new certificates issued for a specific domain name.
3. CT Logs - This website is operated by Google and provides a list of all CT logs that are currently in operation, as well as information on how to submit certificates to the logs.
4. SSLMate - This website provides a list of CT logs that SSLMate supports and also gives the user the ability to monitor the logs.
5. CT Log Viewer - This website is a tool that allows you to view the contents of CT logs and search for specific certificates.
6. CertStream - This website provides a real-time feed of all certificates seen by publicly trusted CT logs.
These are just a few examples of websites that provide information and tools related to certificate transparency.
Omar created a convenient tool that will allow you to get very useful information from certificate transparency records called CertSPY.